FAQ
My name is Colin Hamill, and I am the owner and IT solutions designer for Sentinel Forge Technologies.
I’ve spent more than 15 years designing complex IT solutions to help solve the problems of organizations both large and small.
That is the most important question, and one that can be challenging in our current zero-trust cybersecurity world.
I hope that many will come to trust me because of the reason that I decided to start my own company: I feared for the future of our digital civilization if the current epidemic of cyberattacks is not stopped. My company was formed to make the world safe from all Ransomware & Cyberattacks, for all people, for all communities, for all time.
On a personal level, I am an IT Solutions designer with more than 15 years’ experience in designing ransomware protection solutions for organizations both large and small. I am married to my college sweetheart, and together we have a 6-year-old son that shares the same birthday that I do.
I am an Eagle Scout, both of my grandfathers served in the Pacific Theater in WWII, and I’ve always believed wholeheartedly in the idea of serving & protecting something larger than oneself.
The hackers that we face are bullies that target vulnerable individuals, just like my parents, who they consider to be “unsophisticated” and “easy targets”, which justifies their being victimized. I have a very low opinion of people that pick on the weak, and I felt that I could no longer stand on the sidelines and allow the current state of affairs to continue.
I worry about my parents & my wife’s parents. Older individuals that didn’t grow up with computers & the internet are being forced to participate in our always-on digital world, and our hacker adversaries consider them to be “low hanging fruit” for their cyberattacks.
What really keeps me up at night is the idea of catastrophic disruptions to our nation’s food supply, caused by widespread cyberattacks on the agricultural supply chain & our nation’s farming community. Many family-owned farms do not have the ability to spend millions of dollars each year on modern cybersecurity solutions and have been largely left to fend for themselves.
I personally don’t know how to grow my own food, and I suspect that is the case for most people. If we end up cut off from our food supply, we will all be dead in three weeks.
Most of the hacker groups that you hear about in the news, like DarkSide, REvil, and LockBit, are highly organized & sophisticated criminal organizations, that consider Ransomware & Cyberattacks to be high profitable activities that offer a high rate of return and (relatively) low physical risks.
Many of these groups are located overseas, many operating out of Russia, China, and many parts of Eastern Europe. Some of them have overt or covert support of powerful & unfriendly authoritarian nation states, who provide the criminal hackers with Espionage-grade hacking tools for use in their attacks.
As of 2021, the top 10 Countries where security hackers come from:
- China
- Brazil
- Russia
- Poland
- Iran
- India
- Nigeria
- Vietnam
- USA
- Germany
This website has a very good writeup on the different types of hackers:
https://www.cyberkite.com.au/post/hackers-top-10-countries-where-they-come-from-hacker-types
Any computer that is connected to a computer network is potentially a hiding spot for a hacker. With more and more home devices adding a computer & an internet connection to become “Smart Home Devices”, hackers now have more potential targets to exploit.
This article lists some surprising places that hackers can hide:
- 3rd Party / Off-brand apps
- Your smart refrigerator
- Your car
- Your social media accounts
- Any Point-of-Sale systems / payment terminals you use
- Your Baby Monitor
- Your fax machine
Hackers are very sophisticated and persistent, so it is wise to never think of a given piece of technology as being “unhackable”.
Malware can infect a very long list of different file types, and hackers are actively developing new delivery methods as we learn how to defend against their old attacks.
This article lists the most popular places for Malware to be found today:
- In malicious email attachments
- In malicious links sent in emails (phishing emails)
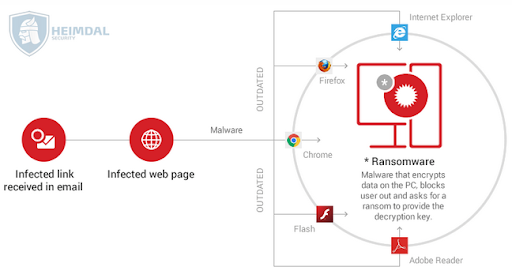
Ransomware Infographic | source: heimdalsecurity.com
- In traffic redirects
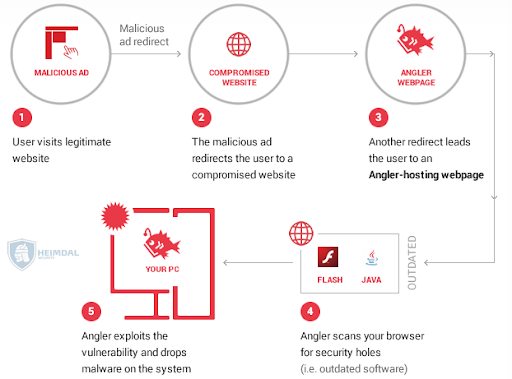
Malicious Ad Redirect Infographic | source: heimdalsecurity.com
- In “free” software downloads
- In online ads
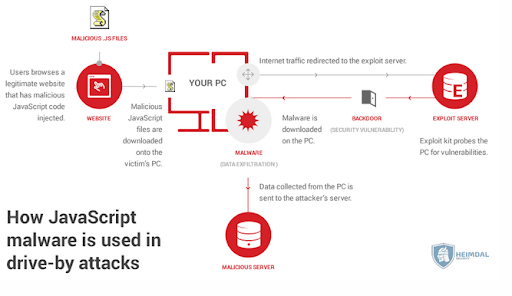
Javascript Malware Infographic | source: heimdalsecurity.com
- On infected websites
- In Torrent Downloads – for “free” software, movies, games, or other “free” digital content
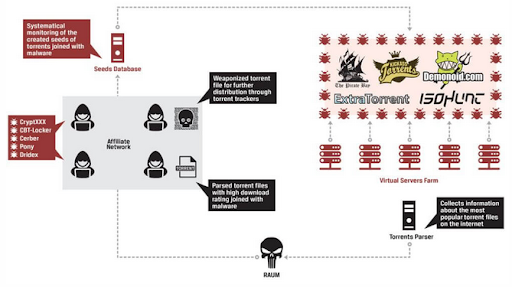
Malicious Torrent Downloads Infographic
- In infected software updates / fake update prompts
- In fake “Free Wi-fi” Hotspots
- In Pop-ups
- In social media posts & messages
- In various files (.txt, .pdf, .jpg, .gif, .zip, .rar, mp3, .mov, .exe, .html, and many more)
- In shortcuts
- In infected web browser add-ons and plugins
- In hacking tools / hacking websites
- In infected USB sticks
A Sentinel Box first product offering from Sentinel Forge Technologies, and it’s intended to be a no-touch affordable & reliable early-warning system for cyberattacks on your IT environment.
The Sentinel Box is an implementation of my proprietary cybersecurity architecture, the Secure Sentinel Network (SSN). The idea is that all of the needed hardware & software components that are required to support the locally deployed Sentinels are inside of the “Box”.
A Sentinel is the term that we use to refer to the decoy & trap workloads that are deployed in a Protected Location as part of a Sentinel Box deployment.
The Sentinel Box service changes the rules of the game for malicious hackers, by concealing multiple decoy systems, called Sentinels, that act as “bait” for cyberattacks & provide early warnings to the presence of malicious hackers inside your network’s cybersecurity defenses.
Most major cyberattacks can take as many as 4-6 months to successfully execute and are extremely vulnerable to being detected by the Defender before the hackers are ready to attack. By saturating the Tenant’s Protected Location(s) with Sentinels that the hackers have no way of knowing about, we can change cyberattacks from something that is “easy to do” into something that is “impossible to do”.
Sentinels are traps that are 100% impossible for a hacker to evade, regardless of their intelligence or the amount of computer resources at their disposal.
It is mathematically impossible for a malicious attacker to utilize some sort of computer-assisted scanning process to check if something is a Sentinel without also generating behavior or activity that is itself detectable by the Sentinel.
Good question…
The same way you safely run through a live-minefield while blind-folded.
I have absolutely no idea.
The term Cyber911 refers to an individual that is considered to be a person’s “lifeline” for technical questions relating to computers or cybersecurity concerns. This is the person that you would call if you personally were hacked, your critical data & banking information was encrypted, and you have 10 hours to pay a $3,000 ransom before your data gets deleted.
This question is best answered by a person’s own Cyber911, but as a rule, you should call your Cyber911 whenever you have any concerns about any computer or cybersecurity related issues.
Your Cyber911 has volunteered to make themselves available to assist in those kinds of matters, so please be sure to make use of it! My policy is “better safe than sorry”!
In a cyber emergency, you will be facing a highly stressful situation, where all of your most important data is at risk of being corrupted & lost forever or paying large ransoms that they cannot afford.
This is not the time to be trying to figure out who could possibly help you, especially in the face of ransom deadlines that can be measured in hours.
Additionally, hackers have also begun corrupting their victim’s cell phones & their contact lists, to further complicate any attempts to seek help. How many of your friends’ & work contacts’ cell phone numbers can you recite without looking them up?
This is why we don’t just recommend designating a Cyber911, but to also write down all of their contact information out on paper, so that you will always be able to get ahold of them in an emergency.
None. 100% of the required computer hardware for the Sentinel Box service will be included in the monthly all-inclusive subscription. The Sentinel Box equipment is owned by the Relay, is deployed at the Tenant’s Protected Location(s), and is the responsibility of the Relay to provide ongoing support & maintenance for their deployed Sentinel Boxes.
The Tenant’s responsibilities are to work with their Relay and heed any recommendations that their Relay has on ways to improve their “cyber hygiene” when using a computer & the internet. Tenants are responsible for leaving the deployed Sentinel Box infrastructure alone, and to not attempt to interfere with its operation in any way.
The Sentinel Box service is billed monthly, and includes the following:
- All required computer hardware & software modules
- The “baseline population” of Sentinels, individualized to fit your environment
- Equal access to all cybersecurity countermeasures & attacker signatures generated using the SSN
- All required support & ongoing support services
- All future updates to the SSN platform
- The opportunity to become a Relay and resell your own version of the Sentinel Box service
Subscriptions to the Sentinel Box service are currently only available in Maryland. The intent is to systematically expand the locations where the Sentinel Box service is available as additional Relays come online in different areas, which will ensure the availability of onsite services, as needed.
Unfortunately, the first warning that most victims of cyberattacks receive is the ransom email from the hacker, or the massive charge on an account that wasn’t caught until it was too late. At that point in the attack, the hacker has effectively already won, and the victim is likely to have few, if any, options besides paying the ransom or losing 100% of their critical business data.
As a rule of thumb, most cyberattacks take around 4-6 months, between “hacker first gains entry to the network” and “hacker executes large-scale Colonial Pipeline level ransomware attack” to successfully execute. One can estimate when the initial breach occurred by working backwards from the date that a ransom was given.
A Sentinel Box Security Reset Token (SRT) is used to activate the automatic security shutdown system included with every Sentinel Box. This shutdown feature is only intended to be used for legitimate emergencies where the Sentinel Box at a Protected Site needs to be reset.
The reason that these Sentinel Box SRTs are used is to limit the ability of adversaries to attack the Sentinel Box SRT system with DDoS attacks.
You will typically receive all newly generated Sentinel Box SRTs within two (2) hours of requesting it through the online portal. Phone & email requests will typically take longer than two (2) hours but will typically be completed on the same day they are requested.
If you have not received your Sentinel Box SRT within two (2) hours of requesting one, first check your spam filter & firewall to make sure that it wasn’t caught.
If that doesn’t solve the problem, simply reach out to the SRT Customer Service team at SRTsupport@sentinelforgetech.com, who will assist you with getting your Sentinel Box SRT generated & delivered as quickly as possible.
Any existing Tenant that meets the requirements to be a Relay and has the recommendation of an existing Relay will be given the opportunity to become a Relay themselves.
Becoming a Relay means taking on a large amount of responsibility and being willing to join a group dedicated to protecting the members of the SSN, and to making the world safe from all ransomware & cyberattacks.
The Sentinel Box hardware will be deployed at every designated Protected Location, in locations approved by the Tenant. The hardware will typically be deployed in the same location where your internet service comes into your home or next to a home computer.
The Sentinel Boxes are intended to be unobtrusive and are built using computers with smaller form factors. Your Relay will work with you as part of the initial network assessment to determine the specific location for each Sentinel Box to be deployed and to make sure that the box “fits in” with the Tenant’s location.
Not all of us have an easy time remembering passwords, and if you must write your passwords down, then go ahead and do that. Paper copies have the advantage of being 100% unhackable and are the ultimate “air gap” from a cyberattack.
My only recommendation would be to be VERY careful with where you keep the written copies of your passwords. As an example, my mother-in-law has a plain little nondescript address book where she keeps all of her household accounts & passwords.
The book is kept right next to their home computer, which is in a secure location inside of their home. She is confident that hackers are not going to physically break into her house to steal her password book.
She also has the peace-of-mind of knowing that her family would be able to locate & access all of her different accounts if something were to happen to her.
The Sentinel Box service is not intended to be a replacement for any existing cybersecurity defenses. The Sentinel Box service actually depends on those existing defenses remaining in place and making it difficult for malicious adversaries to break into an environment.
The average cybersecurity attack takes approximately 4-6 months to fully execute, in large part because of the cybersecurity defenses that are in place today.
The Sentinel Box service actually depends on your existing cybersecurity defenses, keeping hacking a “hard thing to do” and make successful cyberattacks take 4-6 months to successfully pull off.
The Sentinel Boxes themselves will be built using the Tenant’s existing monitoring & other software tools, where possible. The goal is to minimize the upfront costs of the initial Sentinel Box deployment and to take advantage of the Tenant’s familiarity & training with existing software tools.
I am only a single person and my ability to directly sell my Sentinel Box service to others is limited by the number of people that know & trust me, as well as my geographical location. The threat to our society by unchecked cyberattacks is a global one, and it will require us to work together to defend ourselves.
Allowing other MSPs, MSSPs, VARs, and driven individuals to resell my SSN IP allows it to spread much quicker, and in a highly distributed & decentralized fashion that will make it impossible for hackers to attack effectively.
The more that hackers persist in launching cyberattacks on computer networks that are connected to the SSN, the more we will learn about their tactics, tools, and techniques, and the less effective those things will be in launching future attacks.
The end goal is to make ransomware & cyberattacks into an unproductive & unprofitable use of their time, and they will move onto something else. This is the same reason why organized crime doesn’t consider rum-smuggling & bootlegging to be something that they still do.
Partially to encourage the adoption of the SSN platform, which will allow the formation of a robust SSN “ecosystem”, which provides superior protection as more nodes are added to the network.
I also feel that the Sentinel Relays are the ones taking on the responsibility of keeping their Tenants safe from harm and are the ones taking the risks & putting in the hard work of building their own businesses. Relays are also responsible for periodically upgrading & updating their deployed Sentinel Boxes with newer hardware, with the cost of those upgrades expected to be funded by their active Sentinel Box service subscriptions.
I believe the Relay’s effort should be rewarded by allowing them to keep the overwhelming majority of what they earn.
The 5% licensing fee will be used for my own income (I’m not doing this for free!), for the continued development of new cybersecurity countermeasures using attacker data collected from the SSN, and to enable the equal distribution of developed countermeasures & attacker signature data to all members of the SSN.
Stay Connected!
Sign up to receive tips, information about upcoming events, industry insights and more!
